[! My notes are gathered from academy.hackthebox.com and nmap.org]
Description

Nmap is a tool that every hacker needs in their toolkit as it’s on the road to enumerating a system. In fact, I would consider this as the first step when you’re conducting a pentest.
Scan Types
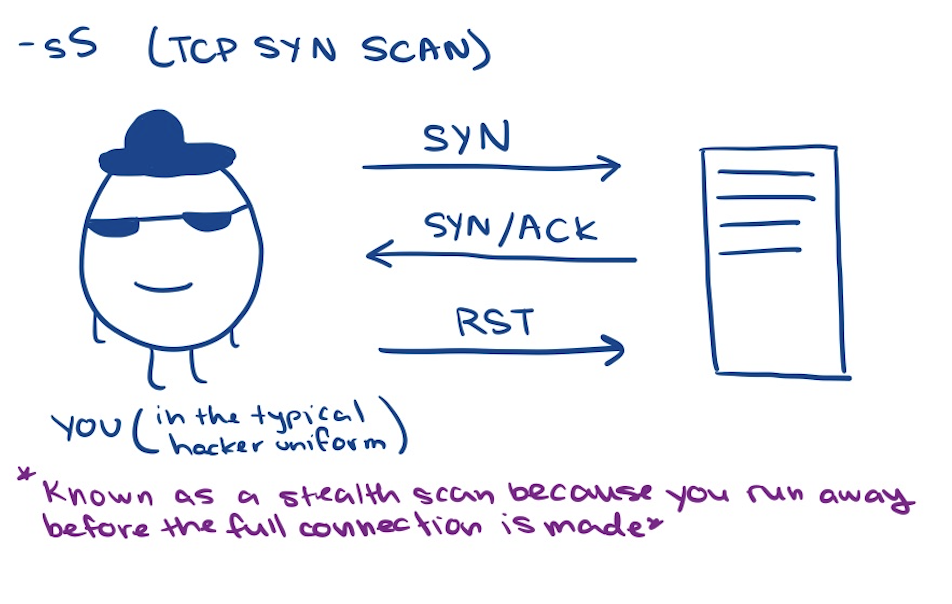
-sS (TCP SYN scan)
- does not complete the three-way handshake as it only sends a SYN packet and waits to receive a SYN-ACK packet (signifying an open port) or RST packet (signifying a closed port)
- no packet in nmap means the port has a filtered status and you do not know whether the port is closed or open and further testing is required (could be a firewall blocking packets)
- quick scan, stealthy because it doesn’t complete the three-way handshake
 -sT (Connect scan)
-sT (Connect scan) - nmap uses the operating system to connect to the target and port using connect call
- not the most stealthy
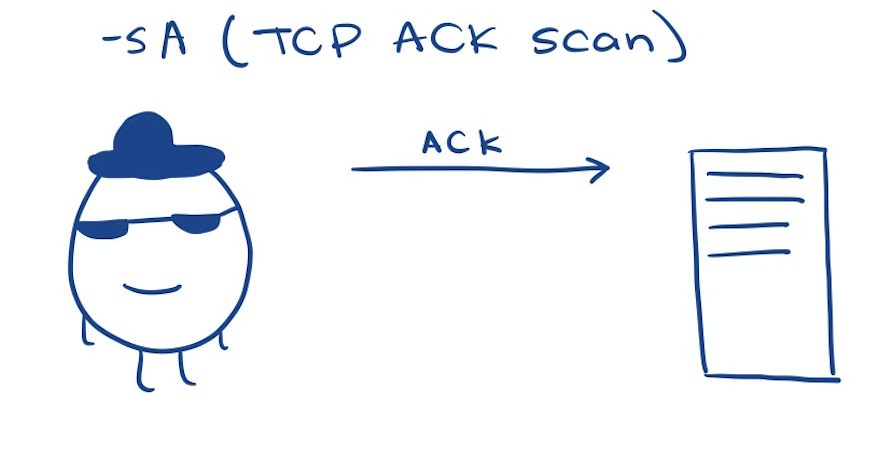
-sA (ACK scan)
- sends ACK packet and waits to receive a RST (indicating that it’s open or closed), no response (meaning the port is filtered), or an error (meaning the port is filtered)
- this scan is useful for mapping firewall rules because the firewall can’t figure out if the connection is from the external or internal network
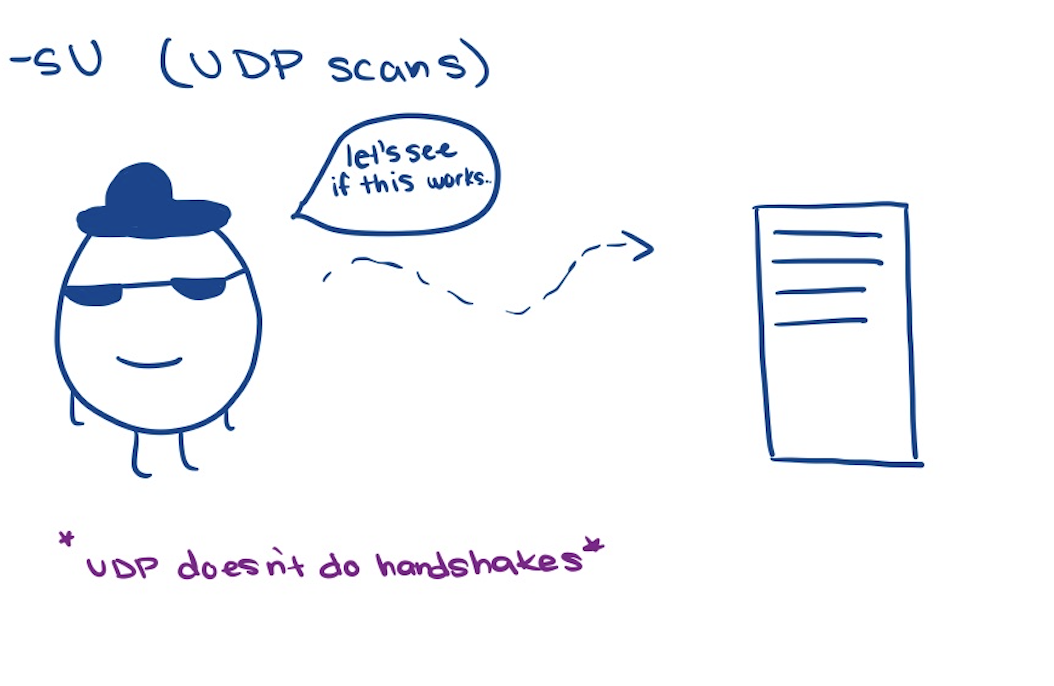
-sU (UDP scan)
- scans for UDP services
- slower
- sends UDP packet
- only know if the port is open if the application is configured to send out responses
Helpful Options
| Option | Description |
|---|---|
| -sn | disables port scanning - sends ping scan with ICMP echo requests (-PE) |
| -PE | scans with ICMP echo requests |
| -iL | performs scan from provided list |
| —disable-arp-ping | disable ARP pings and ping with ICMP echo requests instead |
| —top-ports=? | specify the number of the most frequent nmap-defined ports you want to scan |
| -p- | scan all ports |
| -F | top 100 ports with fast scanning |
| -n | disables DNS resolution |
| —packet-trace | to show all packets in the communication |
| -sV | more information including versions, service names, etc. |
| —reason | why a port is set to a specific state |
| -Pn | disables ICMP echo requests |
| -oN | save as .nmap file |
| -oG | save as .gnmap file (grepable) |
| -oX | save as .xml file |
| -oA | save in all formats |
| —script __ -sC | using nmap’s scipting engine script (auth, broadcast, brute, discovery, intrusive, version, vuln, fuzzer, external, etc.) using nmap’s scipting engine default scripts |
| -T 0-5 | how fast you want to perform the scan |
| —min-parallelism | what frequency to send out packets |
| —min-rate | how many packets to send at the same time |
| —max-rtt-timeout | timeouts for packets |
| —max-retries | number of retries |
Nmap performs service enumeration by looking at the banners or through nmap’s signature-based matching database. You can use tcpdump or nc for obtaining more information about the services
Evading Firewalls and IDS/IPS
- start by scanning with a single virtual private server (VPS) and use a different VPS if the host is blocked
- use decoys (using -D) for nmap to generate random IP addresses in addition to our IP address so the server is confused about what the exact origin packet is
- specifying a source IP address (using -S) from inside the same network range
- specify the —source-port as 53, which specifies the DNS servers (more trusted than those coming from the Internet)
