These are my main takeaways from Practical Vulnerability Management: A Strategic Approach to Managing Cyber Risk by Andrew Magnusson
I’m a little biased here (as I’m currently a vulnerability management engineer for my organization), but vulnerability management plays an integral role in a company’s security program and is part of its overall risk management goals
The Vulnerability Lifecycle
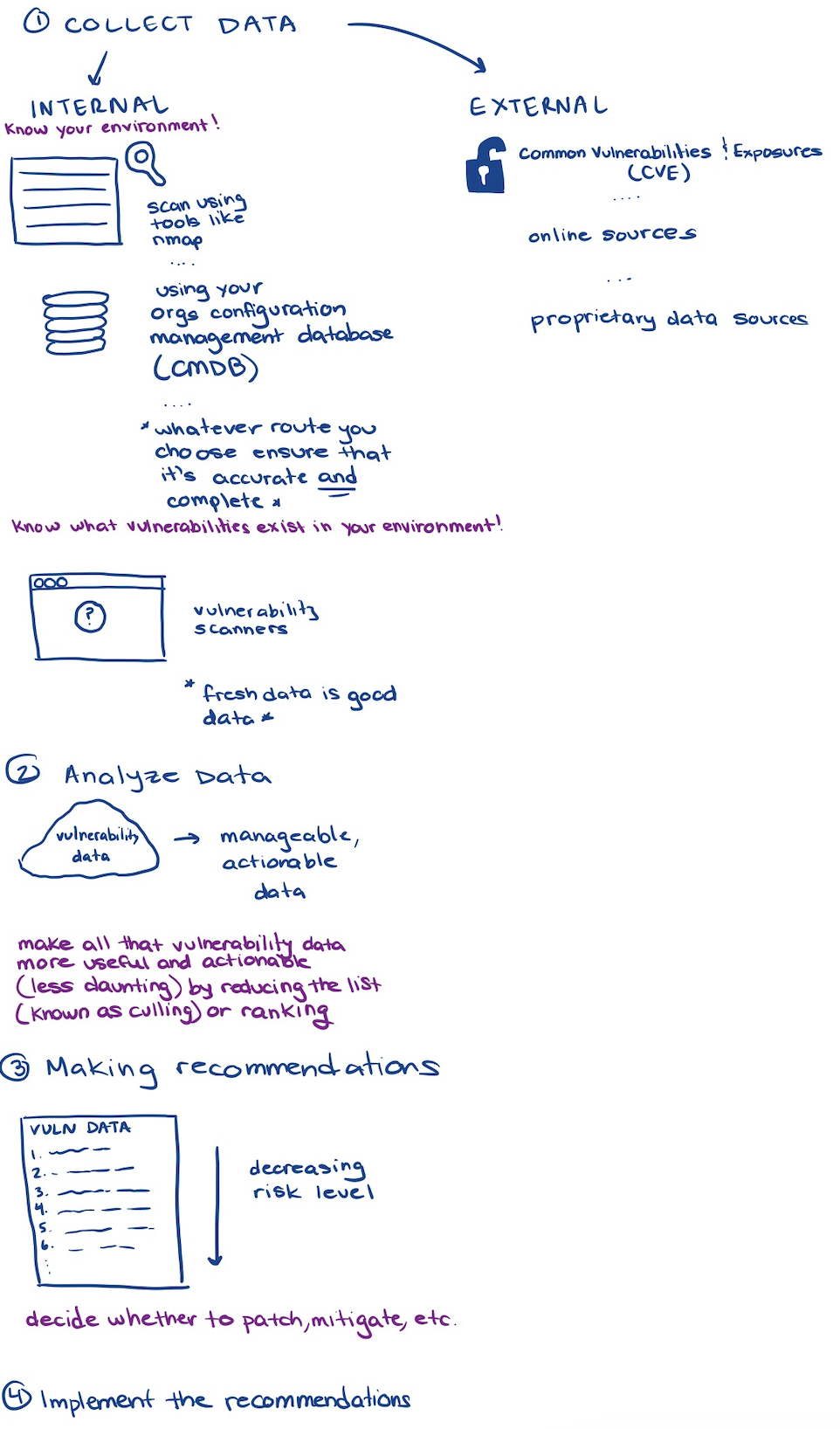
asset information (list of hosts) can be gained using
- network scanning tools (Nmap)
- CMDB
- by performing discovery scans using vulnerability scanners (Nessus, Qualys)
- should be run on a schedule
vulnerability information can be gained using
- a vulnerability scanner that performs a complete vulnerability scan
- configuring and scheduling scans is its own science and should be tailored to the enterprise
exploit data can be gained using
- the exploit database website
- Metasploit for usable exploits
- CVE database (by MITRE)
- threat intelligence feeds
- proprietary exploits
- network configurations
what to do with vulnerabilities when found
- patching: finding the solution to a problem (including updating a system)
- mitigation: finding a way to solve the problem by lessening the vulnerability’s impact (including implementing a control)
- systemic measures: broader solutions that improve the entire enterprise’s security posture
- accepting risk: decide that the risk is acceptable and not doing anything about the vulnerability
- defense in depth: putting more than one defense in place to combat the vulnerability
what to do after you have taken action (or inaction in the case of accepting risk) against the vulnerability:
- validate the controls: make sure that the controls you put work against the vulnerability!
